
Dynamic AI is available in 4 different editions:
Dynamic AI Personal
Dynamic AI Desktop
Dynamic AI Server
Dynamic AI Enterprise
This chapter focuses only on Server and Enterprise editions.
In order to understand the differences between the different server types it’s important to understand the fundamental architecture of the Dynamic AI application.
Dynamic AI is a centrally installed application server service hosted by the Microsoft Internet Information Services (IIS). IIS is part of Microsoft Windows. The Personal and Desktop editions can also run under Quickweb desktop web server.
The diagram below illustrates a scenario with Dynamic AI installed on a server PC and connected to an Oracle database, a Microsoft Access Database and a Microsoft SQL Server:

The Dynamic AI server is the single-point-of-entry for end-users to background databases. The communication between the Dynamic AI server and the Browser clients (illustrated in blue) is pure HTTP or HTTPS traffic. No data-access drivers are used or needs to be installed on the clients. The user-interface including all presented menus, forms, data-relationships, reports, drill-down specifications etc. are dynamically created upon request from the Browser clients and send to the client as pure text, tagged as HTML, DHTML and JavaScript code. Certain charts are sent in a binary format.
The user-interface presented on the client is valid and available only for the current login session. After exiting the browser or selecting log-out (Exit) in the user interface, the content is no longer available for use through the Dynamic AI application itself.
From a security perspective it’s important to note that reports, forms etc. might be cached in the Browser client’s temporary Internet content storage. Certain Proxy server installations might cache information when Dynamic AI are used through a Proxy server installation. In general Dynamic AI content follow the same rules as normal Intranet / Internet content, and can therefore also be protected with SSL encryption and the use of certificates.
Dynamic AI operates under Microsoft Internet Information Services (IIS). IIS should be administered in accordance with the desired security level, for instance by restricting access to the Dynamic AI application web-site only to users having a valid certificate etc.
Dynamic AI in a standard installation (Server or Enterprise) is a secure installation that only requires public sharing with read and executable access to a limited number of “initiating” files.
In order to further protect Dynamic AI a number of features depending on the type of Dynamic AI installation is available as described below.
When installing Dynamic AI Server, all Dynamic AI application components as well as the supporting database storage files are installed onto the Server itself. On the Server installation Dynamic AI will log entries into the Dynamic AI log database files (dnmclog.dai and dnmcvers.dai), store all users, user rights, connection definitions, report and form definitions etc. into the Dynamic AI repository database file (dnmc.dai).
Below is illustrated the significant components of a Dynamic AI server:
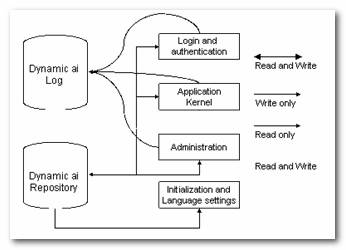
The Dynamic AI Repository (file: dnmc.dai) is the storage file for all installation specific definitions, users, connections, global settings, relationship definitions, dictionary, styles, forms and report components etc. The file is password protected and should not to be accessed from outside the Dynamic AI Professional Server standard browser based user interface.
The Dynamic AI log files (dnmclog.dai and dnmcvers.dai) are installed into the DAT folder during Dynamic AI setup. Dynamic AI stores all user-driven actions (requests made to the Dynamic AI server) from login to logout as well as a snapshot of data when the user makes inserts, deletes or modifications.
The log file will also capture illegal login attempts as well as the IP address of the client attempting to login.
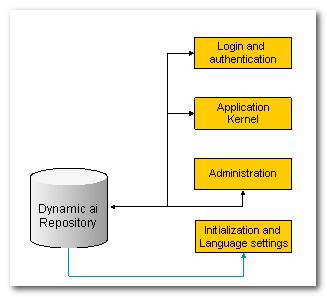
The below diagram illustrates the minimum components to be installed to have a functional Dynamic AI Server installation:
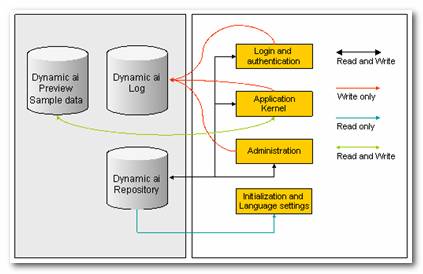
The Dynamic AI Enterprise Edition can be installed in a configuration much like the Server edition, except that the repository, log and versioning data are stored on high performance database servers (Oracle or Microsoft SQL Server).
As the database servers typically are under control of the local IT administration, the Enterprise Server version also allows access to the repository table structure and data as well as detailed log entries for further use and integration.
The Enterprise Server offers enhanced scalability by allowing multiple servers to access the same central repository, log and versioning data (see below) and can take advantage of the enterprise-class database back end’s ability to be backed up on-the-fly.
During setup of a Dynamic AI Enterprise Server, connections to the repository and log database server are specified. The database path, usernames and passwords are encrypted and stored on each Enterprise Server in the file enterprise.ini in the DAT folder.
Below illustrates the Enterprise Server that allows separation of the application components (the white box) and the repository, log and preview data (the gray box).
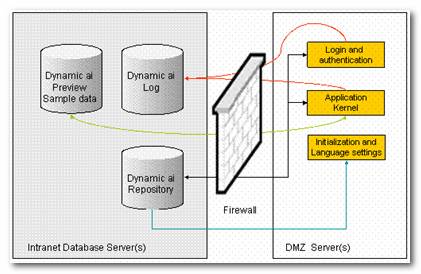
The DMZ (De-Militarized-Zone) server option is a special Enterprise Server configured to have no administrative capabilities, running as a slave server off the Enterprise repository. The DMZ type installation asserts that no administration functionality will be available on the server. It is used in combination with an Enterprise Server, when access to Dynamic AI is needed through the public Internet.
In order to protect the DMZ server from unauthorized use, it is recommended to enforce whatever best practice security standards are required, such as forcing IIS to only accept users having a proper client certificate, encrypt traffic with SSL encryption, and turning on the Client Certificate Organization ID recognition in Dynamic AI itself.
The DMZ installation will ensure that nothing apart from the encrypted path to the repository database, the encrypted username and password for the repository and log databases are stored locally on the Dynamic AI server. The DMZ server will typically be installed in front of the Firewall to the Intranet on which the repository and log database server should be located. The traffic to and from the DMZ application server(s) and the Intranet Repository and log databases will depend on the database provider. For an Oracle based repository, this could be the Oracle Net type of communication which involves a protocol “jump” behind the Dynamic AI DMZ server increasing security.
In order to support scalability for a high number of users, both Intranet and secure Internet use as well as allowing for redundant hard- and software installations, the Dynamic AI Enterprise Server application supports multiple server installations across the same repository.
A possible configuration of more Dynamic AI Enterprise Servers is illustrated below:
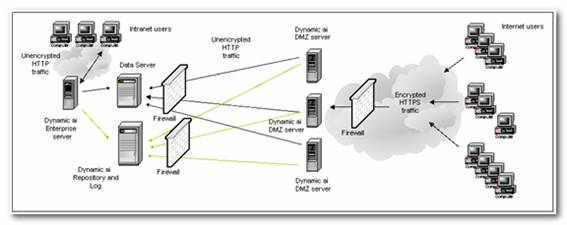
While a Dynamic AI Enterprise Server located on the Intranet gives full administration and customization functionality to authorized users, who can also benefit from running unencrypted traffic across the Intranet, the three DMZ type Enterprise Servers offers a scalable redundant application server environment to the Internet users running encrypted traffic with certificate recognition from both Internet Information Server as well as the Dynamic AI Enterprise application. The DMZ servers do not have administration features installed.
All servers access the same central Dynamic AI repository and log on the “Dynamic AI Repository and Log” database server – which for illustration purposes, have been placed on its own database server, separate from the data server(s). The infrastructure illustrated above can also be supported having the Dynamic AI Repository and Log databases placed on the data server.